What Is URL Blacklist and How to Fix It?

What Is URL Blacklist
A URL blacklist is a list of dangerous URLs, IP addresses, or domain names that authorities have deleted from search results. Search engines like Google and Bing, as well as antivirus service providers like McAfee Site Advisor and Norton Safe Web, are examples of these authorities.
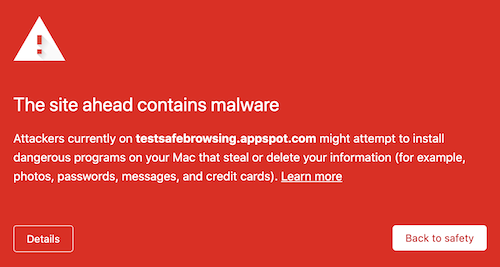
When a URL is blacklisted, people are unable to access it. Instead, they’ll see a red page with a warning message indicating the site is infected with malware.
As a result, having your site banned will have a detrimental influence on its traffic, conversion rates, and reputation. In addition, you won’t be able to use Google Ads.
Security flaws or malicious conduct such as phishing, trojan horses, or spam can lead to URL blacklisting. However, it is not necessarily the responsibility of the site owner. It might occur as a result of cyber-attacks or malfunctioning software.
What Causes a URL to Be Blacklisted?
Authorities ban website URLs for a variety of reasons, ranging from simple errors like installing an insecure plugin to more serious risks like phishing schemes and trojan horse assaults.
Authorities add a notice on the page, asking people to abandon the website, to safeguard users from such URLs.
1. Phishing Content and Schemes
Phishing is a sort of cyber assault aimed at obtaining personal information such as login passwords or bank account information. It entails tricking the user into clicking malicious links or opening malicious attachments.
Phishing links can be embedded in a hacked website; site owners may be unaware that their websites contain harmful links and are punished as a result. As a result, it’s critical to scan your website on a frequent basis in order to detect such an assault.
2. SEO Spam
Overdoing SEO, also known as spamdexing, is a form of SEO spam that has a detrimental influence on your website. It might be as easy as stuffing too many keywords into a piece of material or hacking a website to take advantage of its SEO.
The latter is a harmful act of hacking a well-ranked website in order to stuff keywords and links into search engine results in order to manipulate search engine results and rank the site for keywords that the hacker is targeting. Hackers may also include links that bring users to dangerous or fraudulent websites.
To entice victims to their schemes, a hacker could target phrases regarding a popular product, for example. They would then break into a high-ranking blog or company website and add keywords to rank for product-related search queries. Finally, they provide links that appear to be real in order to lure readers to their fraudulent websites.
These con artists don’t bother trying to rank their websites since search engines have algorithms that identify and dismiss them.
More blog: Dofollow vs Nofollow
3. Malware
Malware is a type of software that hackers use to infiltrate your computer system, steal your data, or make money unlawfully. Authorities will add a site to their URL blacklist if they feel it includes malware or any abnormalities that resemble malicious code.
Malware comes in a variety of forms, each with its own set of characteristics. The following are some of the most frequent types of malware:
Virus: Attackers attach a virus to an executable file, which spreads and infects other files when you open or activate it. This can result in corrupted data and a loss of system functionality.
Trojan horses. Disguised as legitimate software, Trojan horses work inconspicuously and often aim to create a backdoor in your security system for further breach.
Adware. It shows pop-ups and ads that are not relevant to your content. This affects your website performance and annoys your website users. In worse cases, the ads link to phishing websites or files that may contain spyware.
Spyware. As the name suggests, it’s malware that’s hidden from your sight and recording what you do on your computer. This includes collecting credentials information that you type in, such as passwords and credit card numbers.
Ransomware. This malware locks your computer and files. The attacker then threatens that they will publish or delete the data unless the victims pay a sum of money.
Botnets. These are networks of malware-infected computers. Attackers control the network and utilize these computers – or bots – to perform malicious attacks such as spam, click fraud, or distributed denial-of-service (DDoS).
4. Using Harmful Plugins
A plugin is a piece of software that you may put on your website to enhance its functionality. Because anybody may create and sell plugins, they may compromise website security.
It’s critical for website owners to be picky and research the developer’s authenticity and reputation. To obtain access to your website, malicious developers may inject destructive code into the plugin.
Another concern is utilizing obsolete plugins, which may have fewer security layers and are thus more vulnerable to attack.
How Can You Keep Your Website From Being Banned?
Malicious website assaults may appear frightening, but there are certain steps you can take to stop them and avoid being blacklisted.
1. Ensure that everything is up to date.
Never ignore any WordPress update notification, whether it’s for the core, plugins, or themes. These upgrades frequently enhance or repair existing security concerns. If you don’t update them, hackers may be able to break into your site using obsolete security.
Never ignore any WordPress update notification, whether it’s for the core, plugins, or themes. These upgrades frequently enhance or repair existing security concerns. If you don’t update them, hackers may be able to break into your site using obsolete security.
2. Only use software that you can trust.
It’s simple to find free software, plugins, or themes, but you should be cautious. Free software may include viruses or expose your website to attack.
There are a few steps you may take to verify the developers if you wish to get any free software or add-on for your website:
Look at the numbers. Downloads or active installations can indicate how credible the software is.
Check reviews. Look at the software’s customer reviews. This should give you more information about the software and whether it’s safe to use or not.
Search for information. If you can’t find any official reviews, try to Google the software or developer’s name. If you find negative information like “don’t trust this developer,” walk away.
Verify the compatibility. When you choose a WordPress theme or plugin, it’s best to pick one that’s compatible with the most recent version of WordPress.
Check for updates. See when was the last software update and how frequently they happen. For a WordPress theme or plugin, it’s best to choose one updated within the previous six months.
3. Use Strong Passwords
Using secure passwords is another technique to protect your site’s backend. Believe again if you think your password is strong enough to withstand brute force assaults.
A password-cracking specialist revealed a 25-GPU cluster capable of making 350 billion guesses per second in 2012. That’s enough time to guess every eight-character password with upper and lower case letters, digits, and symbols in around five hours.
It’s preferable to have a lengthier password with symbols, numbers, and upper and lower case letters, preferably greater than 12 characters.
Password generators, such as LastPass Password Generator, can help you build strong passwords by allowing you to mix and match characters.
Using the same password for two or more accounts is likewise not advised. If one of your accounts is hacked, the others are not at risk.
LastPass and 1Password are two password managers that can help you save and organize your passwords. This allows you to keep complicated passwords without having to remember them all.
4. Use Google Web Risk API
Google Web Risk API is a Google Cloud service that compares URLs on your site to Google’s list of potentially dangerous websites.
Because there’s a higher danger of having an unsafe URL on a site with a lot of user-generated material, this tool is very beneficial. Google Web Risk assists you in scanning your website for harmful links and removing them to make your site secure.
End of the topic regarding URL Blacklist
Leaving your website vulnerable to cyber-attacks raises the possibility of it being blacklisted. If this occurs, you will lose a significant amount of website traffic, which will have a negative impact on your business. It is possible to keep your site from being blacklisted by keeping all systems up to date, using only trusted software, strong passwords, and scanning the site with tools such as Google Web Risk.
If you discover that the website is on a URL blacklist, you must remove the content or software that is causing the problem. You can do this manually or by using website cleanup services. After that, request a review, and your website will be removed from the URL blacklist if there are no further issues.
We hope this article was useful in teaching you about URL Blacklist. Keep in mind that the best approach is to take preventive measures and constantly improve your website’s security.
If you want to know about any any particular topic please let us know on our Linkedin handle F60 Host we will cover it in our next blog.