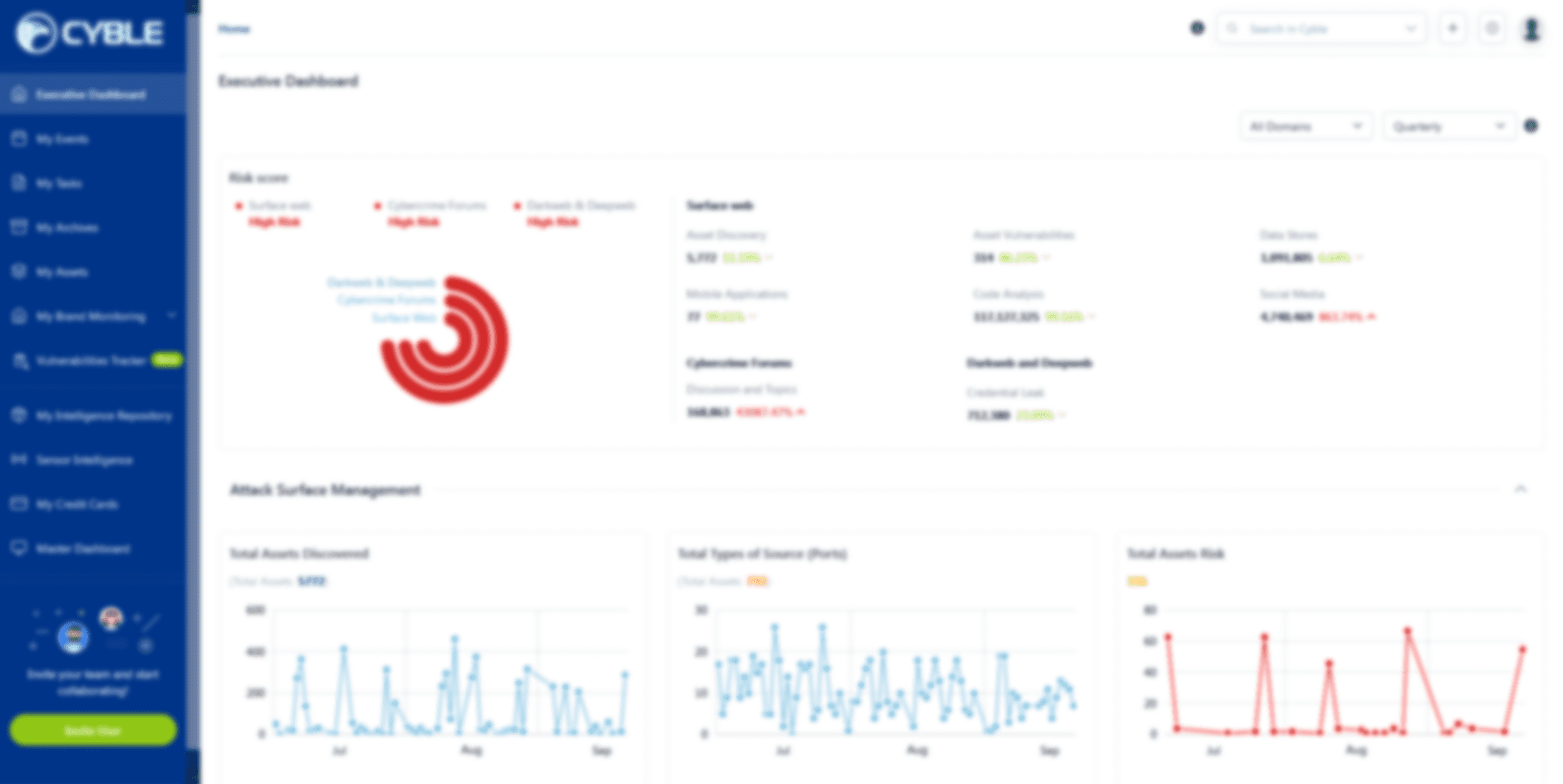
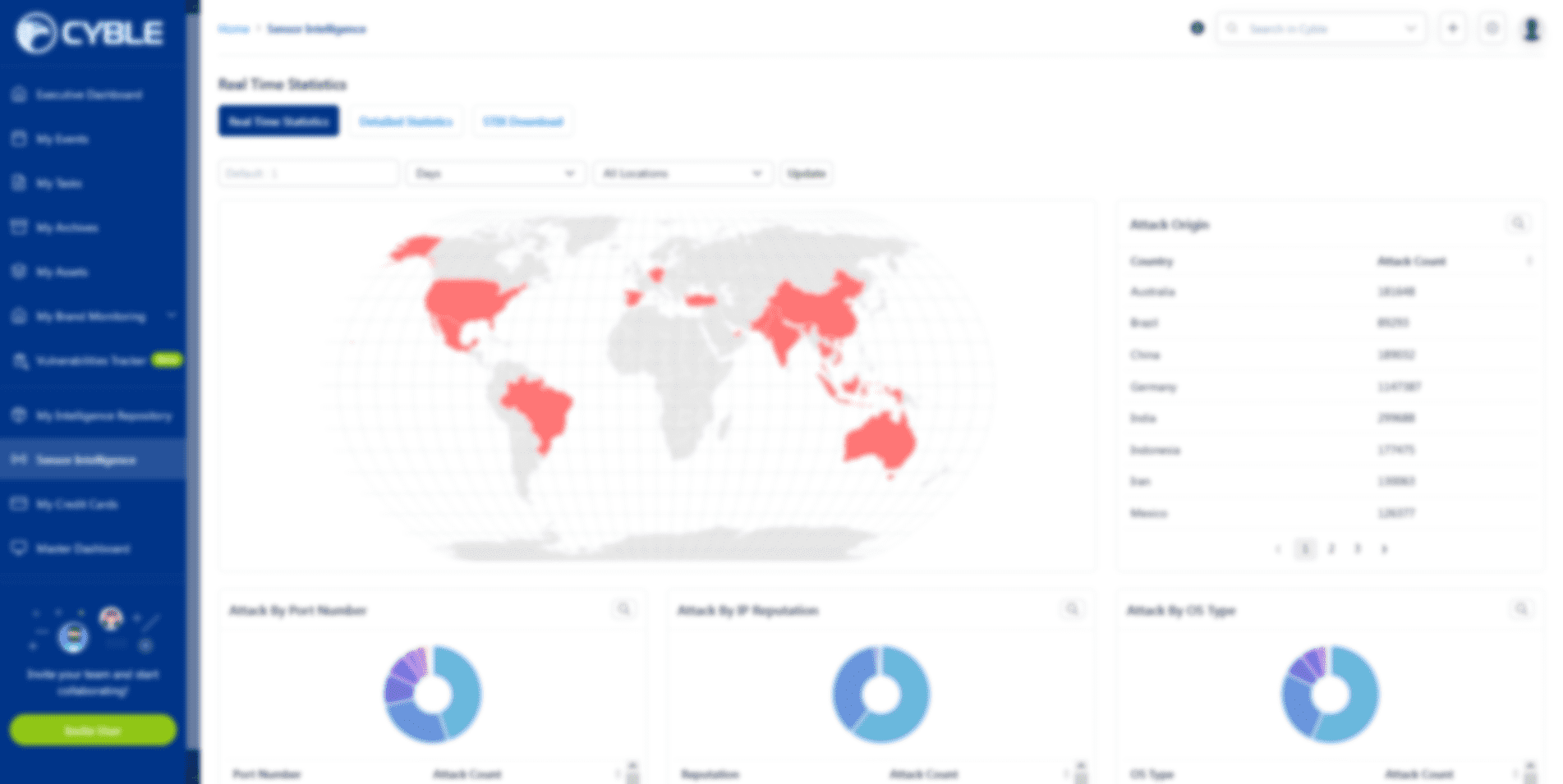
Fraudsters on Telegram are selling Eternity malware tool kits to clients.
Cybercriminals have introduced the ‘Eternity Malware Project,’ a new malware-as-a-service offering in which cyber attackers may buy a malware toolkit Read More ...
May 16, 2022