Honeypots and Honeytraps: Unveiling Cyber Intrusion Detection Tactics

The Importance of Cyber Intrusion Detection in Today’s Digital Landscape
In today’s digital landscape, cyber intrusion detection is vital for protecting our systems and sensitive data. As technology advances, so do cyber threats.
Intrusion detection systems monitor network traffic, identifying suspicious activities and unauthorized access attempts.
Prompt response and detection help prevent data breaches and minimize the impact of cyberattacks.
It also provides valuable insights into emerging threats, enabling organizations to enhance their security. Cyber intrusion detection is an essential part of a comprehensive cybersecurity strategy in our ever-changing digital world.
Understanding Honeypots
Honeypots are decoy systems that attract attackers to gather information about their tactics and motivations.
Unlike traditional security measures, they proactively detect and gather intelligence. They mimic real systems and services, luring attackers into engaging with them and diverting their attention from actual valuable assets.
They are intentionally vulnerable and provide insights into emerging attack methods.
There are different types, including production, research, and high-interaction honeypot, each with unique strengths and use cases. Honeypot enhances cybersecurity defences by identifying vulnerabilities and improving network security.
Types of Honeypots And Honeytraps
There are five varying types of honeypot and Honeytrap deployments
Low-interaction honeypots—Low-interaction honeypot emulates limited services, capturing basic attacker information while minimizing risk. They simulate common services, enticing attackers with restricted access. Benefits include simplicity, easy deployment, reduced maintenance, and minimal network impact. They offer early threat warnings and insights into attacker tactics. Popular examples include Honeyd, Kippo, and Glastopf, enabling lightweight decoy systems and valuable threat intelligence.
High-Interaction Honeypots—High-interaction honeypot offers extensive interaction with attackers, mimicking real systems for deeper insights. They capture detailed data on attacker behaviour and intentions, refining defences. While resource-intensive, they attract skilled attackers. Notable solutions include Capture-HPC, Sebek, and Modern Honey Network (MHN), providing robust frameworks for sophisticated honeypots.
Virtual Honeypots—Virtual honeypot is a software-based instance running on virtual machines. They offer cost-effective and scalable deployment, allowing multiple honeypots on a single host. Cloned and distributed across network segments, they increase detection capabilities. Simulating systems and services, virtual honeypot entices attackers while isolated from the production network. Notable platforms like HoneyDrive, Dionaea, and Honeysnap provide virtualized environments and pre-configured setups. They enable gathering threat intelligence, studying attacker behaviour, and enhancing cybersecurity within controlled virtual environments.
Document and File Honeytraps—Malicious documents and files act as honeytraps to deceive attackers. They contain hidden vulnerabilities or code. When accessed, they trigger malware execution for monitoring. Techniques like sandboxing and virtualization detect and analyze honeytraps safely. Signature-based and behaviour-based analyses identify threats and attacker techniques. Analyzing honeytraps enhances defence mechanisms against real-world threats, revealing attack vectors and exploit techniques.
Network and Service Honeytraps—Network and service honeytraps mimic real services to attract attackers. Deployed within a network, they monitor malicious activities. Simulating open ports, web servers, or databases, they entice attackers. Intrusion detection systems and network monitoring tools identify attacks. Unusual traffic patterns, connection attempts, or unexpected commands indicate attacks. Security professionals gather information to block attackers and strengthen defences. Honeytraps provide insights into threats, trends, and vulnerabilities, enhancing cybersecurity posture.
A Decoy Network: Honeynet
A Honeynet is a network of interconnected honeypots emulating real-world environments. It captures and analyzes cyberattacks on a broader scale. Honeynets attract attackers, diverting attention from production systems.
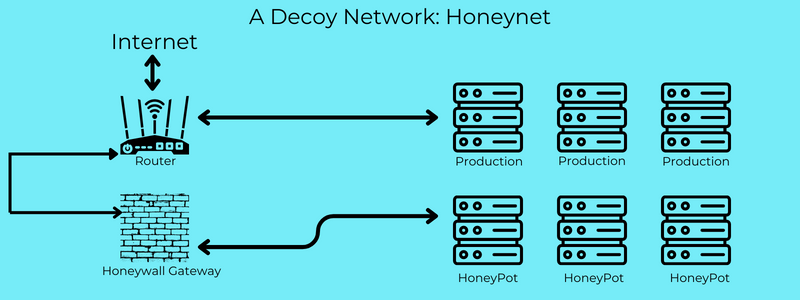
They detect lateral movement and coordinated attacks, providing insights into attacker behaviour. Data collected enhance incident response and proactive defence.
Honeynets promote knowledge sharing and collaboration among cybersecurity professionals. They deepen understanding of attacker methodologies and fortify overall cybersecurity defences in an evolving threat landscape.
Real-world examples where honeypot and honeytraps have been instrumental in detecting and mitigating cyber intrusions
Honeypot and honeytraps have proven to be instrumental in detecting and mitigating cyber intrusions across various industries.
In one notable real-world use case, a financial institution deployed a high-interaction honeypot that mimicked its online banking platform.
By closely monitoring the activities within the honeypot, they were able to detect a sophisticated banking Trojan that had eluded their traditional security measures.
The information gathered from the honeypot allowed them to analyze the malware’s behaviour, develop signatures, and strengthen their defences against future attacks.
In another example, a manufacturing company implemented a network of honeypots within their industrial control system (ICS) environment. This enabled them to identify and mitigate targeted attacks against their critical infrastructure, leading to enhanced incident response capabilities and improved resilience. Additionally, the healthcare industry has benefited from honeypot and honeytraps.
By deploying honeypots that mimic electronic health record (EHR) systems, healthcare organizations have successfully detected and thwarted attempts to exfiltrate patient data, safeguarding sensitive information and preserving patient privacy.
These real-world success stories highlight how honeypot and honeytraps provide valuable insights and early threat detection, and enhance overall cybersecurity in diverse industries, making them powerful tools in the fight against cyber intrusions.
Importance of Honeypots and Honeytraps in Cyber Intrusion Detection
Honeypot and honeytraps are powerful tools for cyber intrusion detection, providing proactive defence and intelligence. By deploying these decoy systems, organizations can lure attackers away from their actual assets, gaining insights into their tactics and motives while minimizing the risk to critical infrastructure.
They divert attackers, minimize risks, and uncover tactics. By studying attacks, vulnerabilities are identified and defences are refined.
Embracing honeypot and honeytraps strengthens cybersecurity strategies, detecting intrusions and enhancing resilience. Explore their implementation to fortify your organization’s security posture and gain valuable insights into emerging threats.
If you’re looking to bolster your cybersecurity strategies, I encourage you to explore the implementation of honeypot and honeytraps further.
By incorporating these techniques into your defence arsenal, you can proactively detect and respond to intrusions, gain valuable threat intelligence, and enhance your overall resilience.
Want to know more? Then follow us at F60 Host



