CloudSEK alleges another cybersecurity firm hacked it.

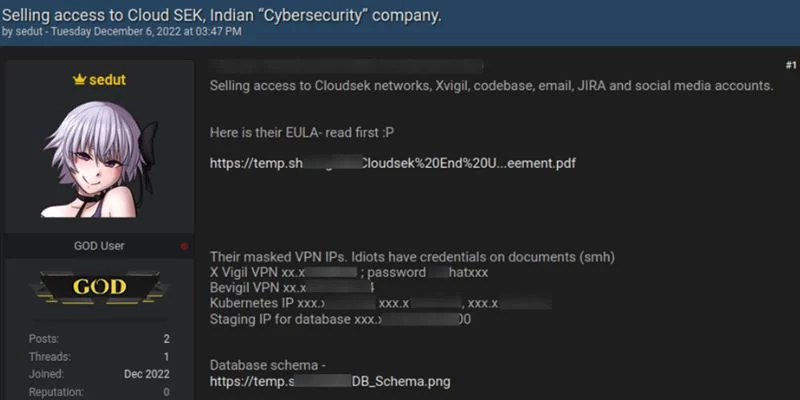
On Tuesday, December 6, 2022, Cyble Research & Intelligence Labs (CRIL) discovered a Threat actor (TA) using the alias ‘sedut’ claiming to have infiltrated the Indian cybersecurity firm CloudSek Info Security Pvt. Ltd., also known as CloudSEK, in numerous cybercrime sites.
According to the post, this looks to be a deliberate attack on CloudSEK with the explicit goal of harming its reputation in the cyber threat intelligence community.
The Threat Actor claims to have many access points and was openly selling them on cybercrime forums. VPN credentials, threat intelligence platform credentials, purchase orders, engineering product-related information, project-related databases, confidential source codes, sensitive infrastructure details, pre-sales information, and detailed clientele information are all included in the package.
For a few months, the TA claimed to have had access to CloudSEK’s environment. To back up their accusations, the TA has given many screenshots and a video demonstrating their access to the company’s platforms and internal servers.
As a result, CloudSEK was fast to launch their own investigation and, within a few hours of the accusations, revealed that the source of the leak was compromised session cookies of a JIRA user, resulting in an account takeover.
The organisation discovered that an employee’s laptop was inadvertently infected with Vidar stealer log malware, which captured passwords and session cookies for accessing their Jira account between November 22-24, 2022.
According to CloudSEK, the TA responsible gained access to the company’s Confluence servers and JIRA platform, three customers’ Purchase Orders (PO), Twitter and Facebook accounts to carry out takedown requests of their clients, client documents, product screenshots from JIRA, training, and internal documents, as well as VPN and endpoint IP addresses.
The corporation denies the TA’s allegations of access to VPN credentials, customer data, and client and staff credentials, stating that the TA’s inferred accesses in their article were drawn from JIRA tickets and internal Confluence pages.
An overview of Threat Actor Claims
CRIL(Cyble Research & Intelligence Labs) investigated the TA’s claims and declarations, and the following is a summary of their claims:
- End-User License Agreement for the Company
- VPN IP address ranges and chastised staff for putting their credentials on documents in their systems.
- Masked IP addresses of the VPN that supports the company’s threat intelligence platform X Vigil, as well as the password.
- The VPN’s hidden IP address, which hosts its asset detection tool, Be Vigil.
- IP addresses of the company’s Kubernetes cluster have been redacted.
- A masked IP address has been assigned to a staging database.
- X Vigil platform database schema, illustrating the backend structure of the company’s monitoring platform.
- The company’s database’s Events Schema, which describes the event workflow.
- Exposed accounts used for scraping cybercrime forums discovered through the JIRA workflow.
- Elastic Search (ES) Dashboard displayed the status of Elastic Search servers, as well as their IP addresses and system use.
- A Purchase Order dated November 3, 2022, received from one of its Indian clients.
- A FoamTree map visualising software components and documentation of the company’s React-based JavaScript (JS) projects.
- Furthermore, TA boasted that they have access to build client accounts in CloudSEK’s X Vigil platform and offered to do so for a fee to anyone contacting them at the email address listed in the post. The TA gave screenshots of administrative access to the platform (seen below). During their inquiry, CloudSEK, however, denied these accusations.
- A video was posted claiming access to the staging platform via an employee’s workstation (SDET – Software Development Engineer in Test), displaying their Google Chrome profile and multiple open tabs. According to CloudSEK’s reaction, the TA most likely received this video from internal documentation / Confluence access.
- In a further attempt to substantiate their claims of access to customer information, the TA issued a list of organisations furnished with a Proof of Concept (POC).
Threat Indicators Against Threat Intelligence Organizations
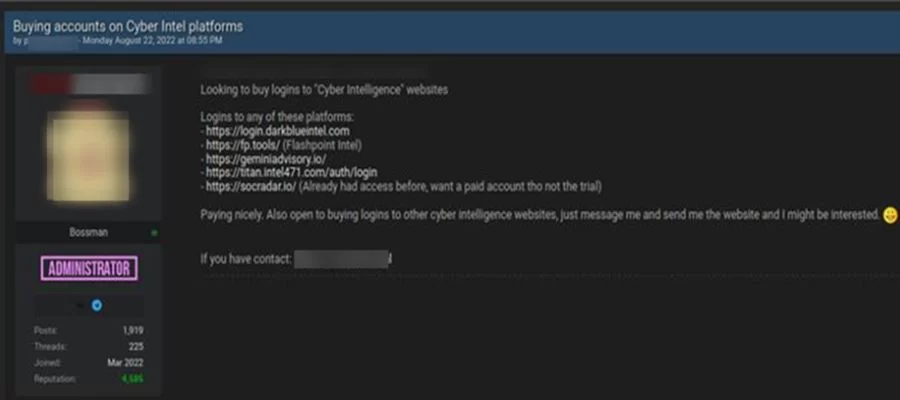
Threat Actors have long been aware of cyber threat intelligence firms. A forum administrator made a topic in August 2022 offering to acquire credentials to Cybersecurity threat intelligence platforms.
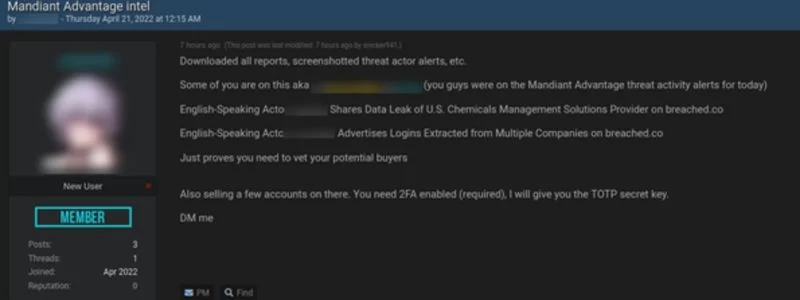
In another incident from April 2022, we noticed a Threat Actor selling credentials to the cybersecurity business Mandiant’s threat intelligence platform. Because the TA eventually left the forum, the claims remain unfounded in the absence of proof.
Information Obtained from Public Sources
The TA’s username,’sedut,’ is a Malay word for “inhale/take in,” suggesting that the TA is Malaysian or otherwise conversant with Malay culture.
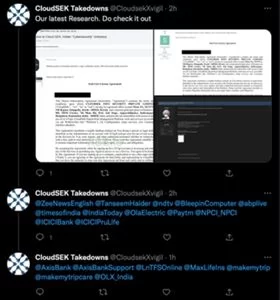
The TA has used the handles “cloudsek takedown,” “CloudsekXVigil,” “Aman Kr,” and “cloud.sek.75” to post on Twitter, Instagram, and Facebook.
According to CloudSEK’s investigation and results, some of the accounts appear to have no relation to CloudSEK or to be utilised to undertake takedown action.
The TA used their social media accounts to share the identical threads they had started on the forums, naming numerous press outlets and CloudSEK customers in the process. The moniker “Cloudsek Takedowns” implies that the TA is actively aiming to ruin CloudSEK’s reputation.
CRIL attempted to explore the TA sedut’s previous antecedents using the email address provided in their article as the point of contact for selling the CloudSEK database.
Our early investigation shows possible linkages to a Threat Actor who was active on RaidForums between October 2017 and February 2022. However, the same could not be confirmed and is still under investigation.
Conclusion – CloudSEK alleges another cybersecurity firm hacked it
The CloudSEK breach indicates a concerning trend of Threat Actors attacking the cyber security and threat intelligence communities. The cat-and-mouse game between threat intelligence firms and cybercriminals has reached a new level, with these actors attempting to destroy their companies’ brand image and reputation.