9 Major Myths Dispelled About Data Encryption
You almost never go a day without hearing about a data breach. Stolen medical records. Hacking of social media accounts. transcripts of education made public. Every sector is vulnerable, and every business is in danger. At best, the outcome can be embarrassing and costly; at worst, it can be totally debilitating, with possible fines, drawn-out legal proceedings, and a consequent decline in customer confidence.
The constant stream of breaches highlights the importance of using encryption as a last resort. But recently, in today’s modern cloud and big data environments, one of the oldest and most effective security strategies has been virtually reduced to a mere afterthought.
This is the result of certain widespread misconceptions regarding the cost, performance, and usability of encryption and key management.
Today, we dispel the nine largest encryption fallacies and put the truth straight.
MYTH 1: Only organizations with compliance requirements should use encryption.
Any business in a regulated sector where data security and privacy are required should encrypt, without a doubt. That is obvious. A better approach to think about encryption is this: regardless of whether there is a legal requirement, you should ALWAYS encrypt data that you deem to be sensitive or competitive, whether it relates to your goods, customers, staff, or market.
MYTH 2: SSL encrypts data everywhere.
SSL does not protect data that is at rest; it only encrypts data that is moving. Data should be encrypted when it is written on a disc, whether it will be kept for a brief moment or several years.
MYTH 3: Encryption is too resource-intensive and difficult.
You can make data encryption as difficult or as simple as you like. Understanding the kinds of data that require encryption, where they reside, and who should have access to them is crucial. On the market, there are many widely available, user-friendly, and reasonably priced encryption tools. Look for a transparent data encryption solution that lies below the application layer and doesn’t require changes to your operating system, application, data, or storage if the
MYTH 4: Database performance will suffer because of encryption.
Encryption is just one of several elements that affect database speed. The performance cost of encryption varies greatly depending on its level, with file-level encryption having a substantially smaller impact. Run block-level encryption on a system with an Intel AES-NI co-processor for the best application performance.
MYTH 5: The cloud is not anymore safe because of encryption.
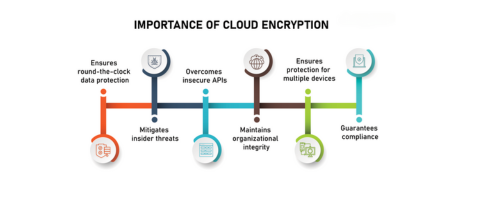
As a matter of fact, maintaining encrypted data on the cloud rather than on-site, where insiders would have easier access, is frequently more secure. Make sure you control the encryption keys, not your cloud provider, to ensure the security of encrypted data stored in the cloud. Find another cloud service if your provider wants you to turn over your keys.
MYTH 6: Data that is encrypted is safe data.
Too many businesses store their encryption keys on the same server as the encrypted data or hand them over to a cloud provider, both of which are ineffective methods of managing their encryption keys. Similar to locking your automobile and leaving the keys inside the door, storing the key on the same server as your data or giving it to your cloud provider is a bad idea. The key to success is effective key management coupled with strict policy enforcement.
MYTH 7: Key management requires expensive, cloud-adverse hardware.
While this used to be the case, today’s organizations can employ key management in the cloud or on-premises thanks to efficient software-based solutions. These solutions can often be implemented much more quickly than hardware security modules (HSMs), are great for the cloud, and adhere to the majority of compliance regulations.
MYTH 8: If your data is encrypted, it can’t be stolen.
No security measure can guarantee complete data security. In fact, businesses should operate under the assumption that their data may be hacked at some point in the future and probably will. But since encrypted data cannot be decoded without the key, data encryption can make the breach’s aftermath considerably more tolerable.
MYTH 9: Encryption is outdated. I require more recent security technology to safeguard huge data.

Data encryption is a tried-and-true security method that performs admirably in contemporary NoSQL systems. Sensitive data, such as protected health information (PHI), financial records, and other types of personally identifiable information (PII), will probably be gathered, processed, analyzed, and stored as big data projects go from pilot to production. NoSQL databases use encryption to protect data much like conventional relational database systems do.
Firewalls and VPNs can offer some security against data breaches and theft, but in large data and cloud environments, strong encryption and efficient key management are a necessity. The greatest fallacies have been dispelled, thus there is no longer a justification for not encrypting.



