What Are Three-Factor Of Authentication? 2 Factor v/s 3 Factor Authentication
Three-factor authentication (3FA) is a security mechanism that provides an additional layer of verification beyond the traditional username and password combination used in two-factor authentication(2FA). It requires the user to provide three different types of credentials or factors to prove their identity before granting access to a system, application, or sensitive information.
What is an example of Three-factor authentication?
This category covers the full range of biometrics, including hand geometry, earlobe geometry, iris scans, fingerprint scans, facial recognition, voice recognition, and even ear scans. For instance, cell phones that use facial recognition or fingerprint scanners frequently use biometric information.
The Three Factors Typically Used In Three-Factor Authentication Are:
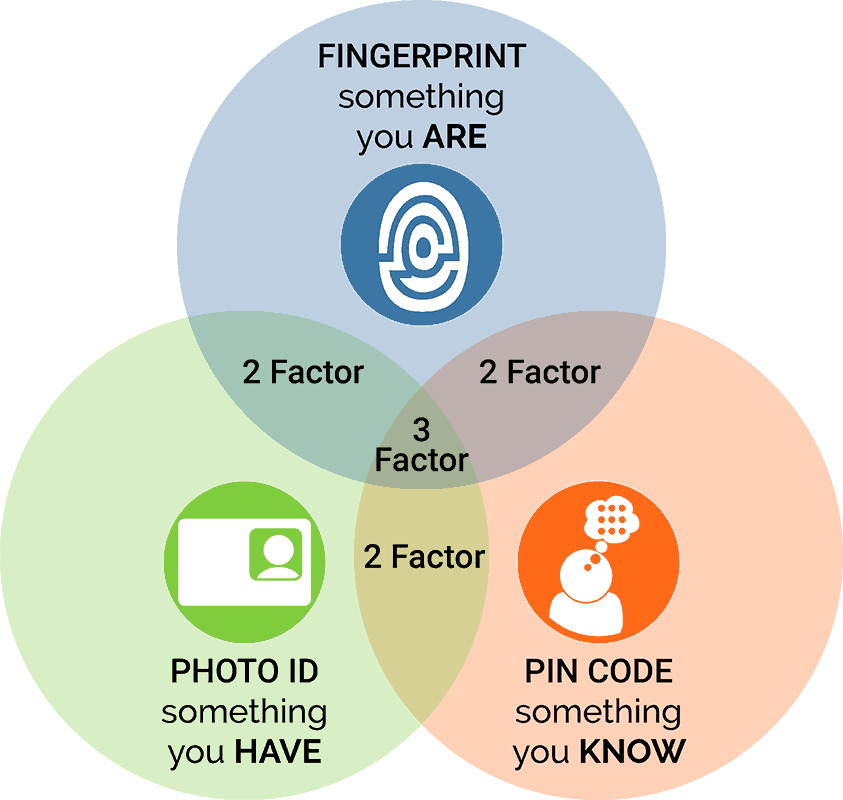
Something the user knows: This refers to a piece of information that the user has knowledge of, such as a password, PIN, or answers to security questions.
Something the user has: This involves a physical item or token that the user possesses, such as a smart card, security key, or a mobile device registered with the authentication system.
Something the user is: This factor relates to the user’s unique physiological or behavioural traits, often known as biometrics. Examples include fingerprint scans, facial recognition, iris scans, and voice recognition.
By combining these three factors, three-factor authentication aims to enhance security by adding an extra layer of complexity for potential attackers to overcome. Even if one factor is compromised, the attacker would still need to bypass the remaining two factors to gain unauthorized access. The main concept of Three-factor authentication (3FA) is to Protect your personal data from cybercriminals.
It’s worth noting that the specific implementation of three-factor authentication can vary depending on the system or service being used. Organizations may choose different combinations of factors based on their security requirements and the capabilities of their authentication systems.
Two-Factor vs Three-Factor Authentication
The main difference between two-factor authentication (2FA) and three-factor authentication (3FA) lies in the number of factors or credentials required to verify a user’s identity. Here are the key distinctions:
Number of factors:
2FA requires the user to provide two different types of credentials, typically something they know (e.g., a password) and something they have (e.g., a verification code sent to their mobile device). On the other hand, 3FA requires the user to provide three different types of credentials, adding an additional factor to the mix.
Additional factor:
The additional factor in 3FA provides an extra layer of security beyond what 2FA offers. While 2FA relies on something the user knows and something they have, 3FA introduces something the user is, such as biometric data (e.g., fingerprint or facial recognition) or other physiological or behavioural traits.
Enhanced security:
With the inclusion of an extra factor, 3FA provides a higher level of security compared to 2FA. Even if one factor is compromised, the attacker would still need to bypass two more factors to gain unauthorized access.
Implementation complexity:
As the number of factors increases, so does the complexity of implementation and user experience. 3FA requires additional infrastructure and capabilities to handle the third factor, such as biometric sensors or specialized hardware. It may also require more user interaction and setup time compared to 2FA.
Contextual adaptation:
Depending on the specific requirements and risk factors involved, organizations may choose to implement either 2FA or 3FA. While 2FA is widely adopted and strikes a balance between security and convenience, 3FA is typically employed in high-security environments or for particularly sensitive information.
In summary, the difference between 2FA and 3FA lies in the number of factors used for authentication, with 3FA offering an additional factor for heightened security but potentially requiring more complex implementation and user interaction. For more details, you may follow us on Twitter.
